Oligo Security researchers have recently brought to light a critical vulnerability, dubbed “0.0.0.0 Day,” which has persisted for 18 years and affects major web browsers like Google Chrome, Firefox, and Apple Safari. Despite its long history, the vulnerability remains unresolved, putting users at risk. Although the browser developers are now working on fixes, the issue still leaves Linux and macOS users vulnerable.
This vulnerability does not impact Windows users but poses a significant threat to those on Linux and macOS. Exploiting this flaw could allow attackers to remotely control affected devices, enabling them to alter settings, access sensitive data, and execute remote code. This makes the vulnerability a major concern for both individuals and organizations alike.
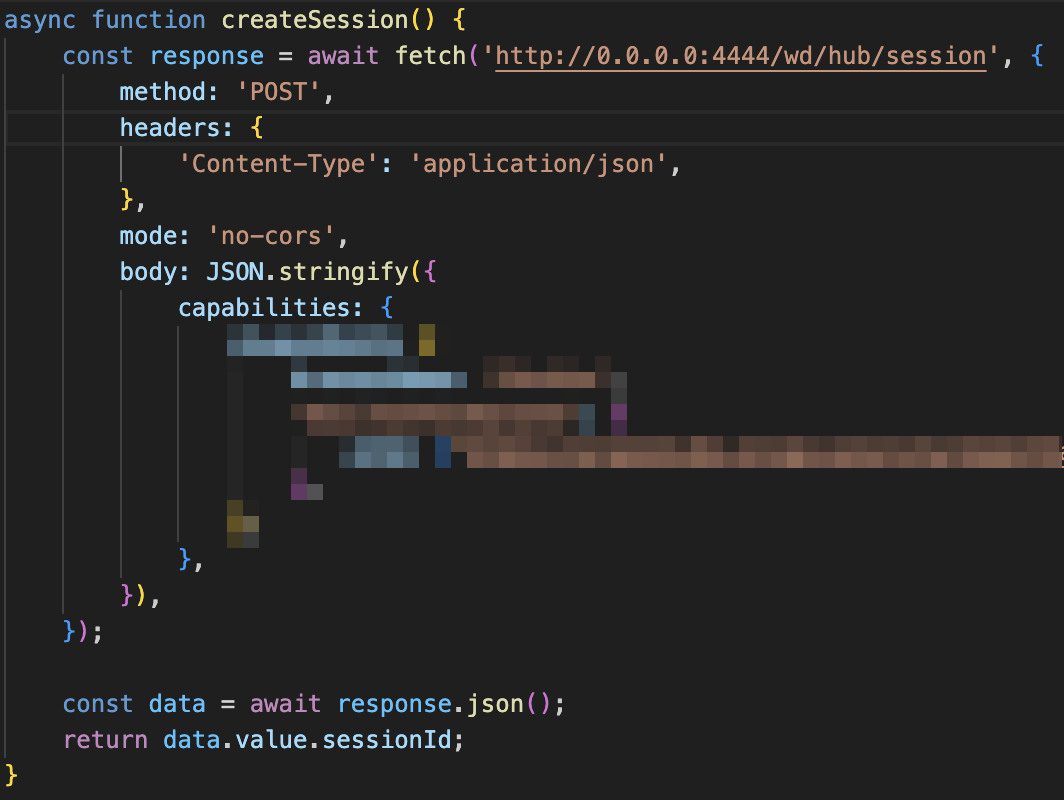
In addition to browsers, a range of applications are also susceptible to this flaw, including popular tools like Selenium Grid, Pytorch Torchserve, and Ray. The underlying cause of the 0.0.0.0 Day vulnerability is the inconsistent security mechanisms across different browsers, which permits public websites to communicate with local network services using the “wildcard” IP address 0.0.0.0.
Critical 18-Year Vulnerability “0.0.0.0 Day” Threatens Major Browsers and Apps on Linux and macOS
The 0.0.0.0 IP address is generally used as a placeholder, but when exploited by malicious entities, it can grant access to local services. A malicious web page could send a request to 0.0.0.0 along with a specified port, which might then be processed by other local services running on that port, making them vulnerable.
Furthermore, this vulnerability can bypass Google’s Private Network Access (PNA) protocol, which was designed to block public websites from accessing private network endpoints.
To combat this threat, web browsers are taking action to block access to the 0.0.0.0 IP address. Google Chrome is rolling out updates to fully block 0.0.0.0 by version 133, while Apple Safari has already implemented measures to block all requests to zeroed IP addresses.
Mozilla Firefox is also updating its fetch specifications and will soon implement PNA to mitigate the risk associated with this long-standing vulnerability.